Facing a problem with Microsoft 365 Defender Data Connector in Sentinel?
A quick post to document an unofficial, hopefully temporary workaround for an "Interaction required" error when configuring the M365 Defender connector.
A lot of my clients and peers have recently been hit with a problem when trying to configure the Defender 365 Data Connector in Microsoft Sentinel.
Even with the correct privileges, opening the connector page results in this error:
There is no way around the error, despite the Sign in again and Ignore buttons. Neither of those will let the user proceed to configure the data connector.
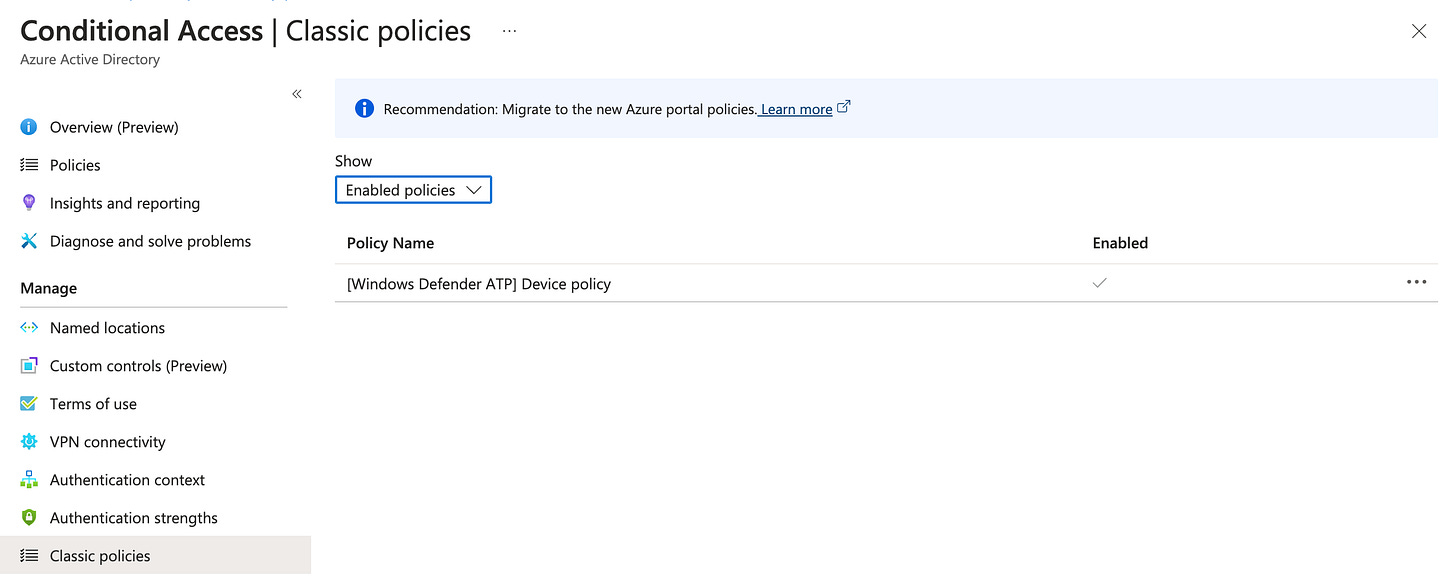
I am discussing this with Microsoft support, and while I don’t have an official fix or explanation from MS yet, I have been made aware by my peers in the security community that the problem is related to the [Windows Defender ATP] Device policy in Conditional Access | Classic policies:
This policy is automatically deployed by Microsoft and is related to the integration between Defender for Endpoint and Intune, as according to this documentation:
“When you integrate a new application to Intune Mobile Threat Defense and enable the connection to Intune, Intune creates a classic conditional access policy in Azure Active Directory. Each MTD app you integrate, including Microsoft Defender for Endpoint or any of our additional MTD partners, creates a new classic conditional access policy. These policies can be ignored, but should not be edited, deleted, or disabled.”
As stated this policy should not be changed by the user.
But, if you are willing to do a temporary unofficial workaround to get the Microsoft 365 Defender connector problem fixed, it seems that excluding Sentinel administrators from the policy helps to circumvent the problem.
You can edit the policy by clicking on the Policy Name and then selecting the group you want to exclude. Individual users can’t be targeted here.
Remember to Save the policy.
After doing this exclusion, the Data Connector page works as expected and you can proceed to configure it:
Reverting the change is easy, as you can remove the group exclusion from the policy.
Note that I don’t have any confirmation from Microsoft on possible side effects from this change and I can provide no warranties here. I have deployed this workaround for a few clients where the need to configure the Data Connector has been urgent.
Hope this is helpful for you if you are hit with this problem, at least to know that others are in the same situation! If editing the connector is not acute for you, you might as well wait for an official acknowledgement of the issue and a proper fix.
Update 19.9.2023:
I got confirmation from MS support back in August, but forgot to update here.
There is no fix as such, but the following workarounds are officially the way to go:
#1 Delete the classic CA policy "[Windows Defender ATP] Device policy"
or
#2 Exclude an admin group from the classic CA policy.





I got confirmation from MS support back in August, but forgot to update here.
There is no fix as such, but the following workarounds are officially the way to go:
#1 Delete the classic CA policy "[Windows Defender ATP] Device policy"
or
#2 Exclude an admin group from the classic CA policy.
Thanks Mikko :)
This information has been a gift that keeps on giving its now September 2024 and this workaround saved me :)
Thanks for sharing your knowledge