Living in a Lighthouse: Defender for Cloud
Azure Lighthouse provides cross-tenant management capabilities in Defender for Cloud. Let's take a brief look at how it works in practice and what the user experience is for security specialists.
Defender for Cloud supports Azure Lighthouse for cross-tenant management.
Users and Groups in the management tenant have full visibility into managed Defender for Cloud environments, as long as Lighthouse has delegated the required access roles.
Compared to Microsoft Sentinel (where you delegate access to the subscription containing the Sentinel workspace) the delegation is more bit more complicated. You need to delegate roles to every subscription that has Defender for Cloud enabled.
After delegation is done, all alerts, inventories, security recommendations and other content in Defender for Cloud is visible by opening the Defender for Cloud portal in the management tenant.
Just remember to set the Azure Portal filter so that you are viewing all subscriptions.
Access roles
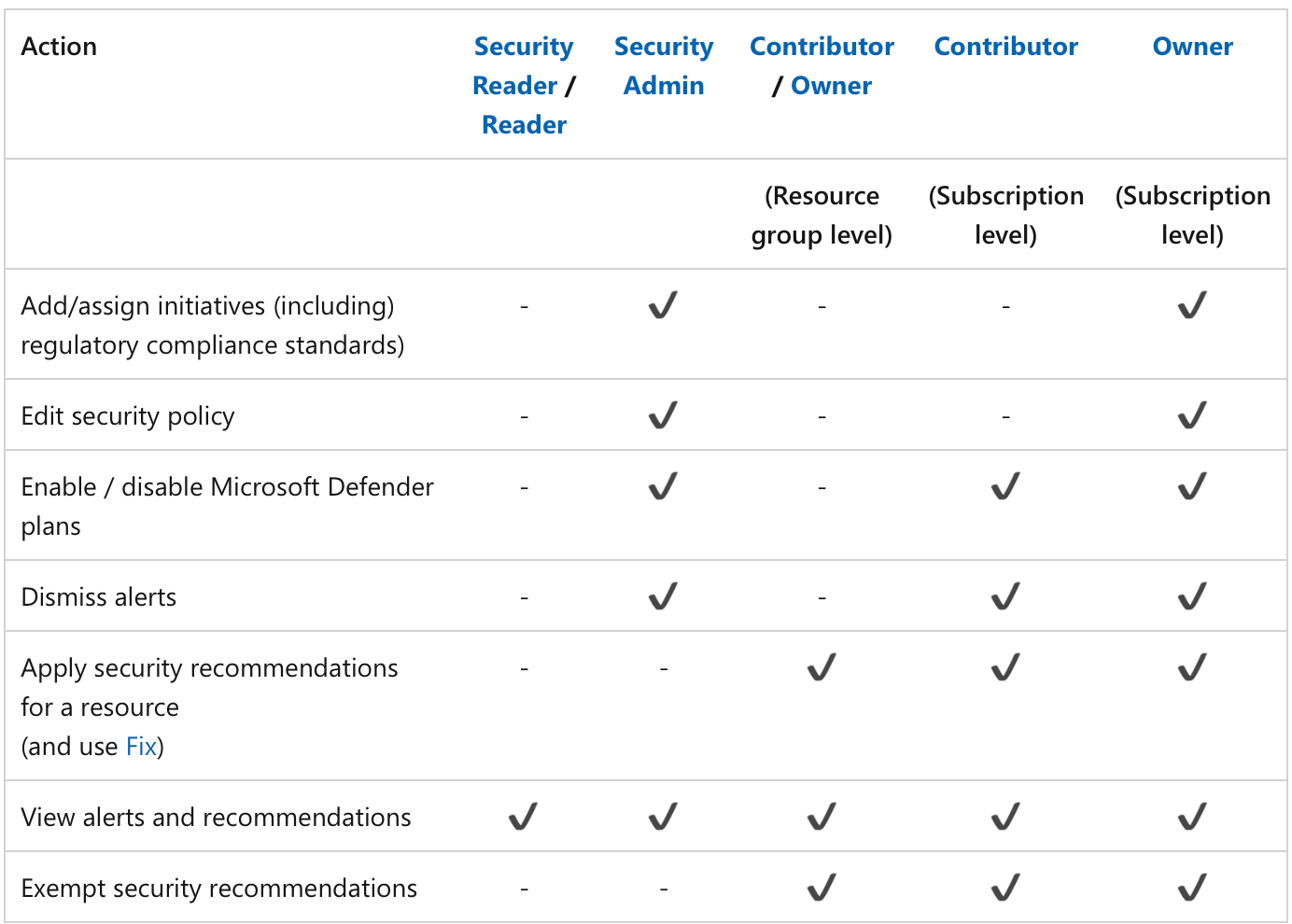
The relevant access roles for Defender for Cloud are well explained in documentation, as shown in the table below.
With Lighthouse you can’t delegate the Owner role, but the other described roles work for managing Defender for Cloud in customer tenants as expected - with some exceptions related to enabling Defender plans, as will be shown in the upcoming Management experience chapter.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/permissions
One thing to note here relates to the navigating Azure resource inventory, which is important to understand when investigating the security posture of managed environments:
The Security Reader role allows you to see the Azure resource inventory inside Defender for Cloud. With this you only see the limited amount of information visible in the security portal.
For full inventory view and read access to resources in Azure Portal, consider delegating the normal Reader role also.
User experience
The user experience for Defender for Cloud does not really change when doing cross-tenant management.
Even in single-tenant cases, you have consolidated visibility to different subscriptions within the same tenant, and can filter the views based on Subscription or Resource Group selection in all parts of the portal.
With Lighthouse and cross-tenant management, you just have more environments visible in the same place.
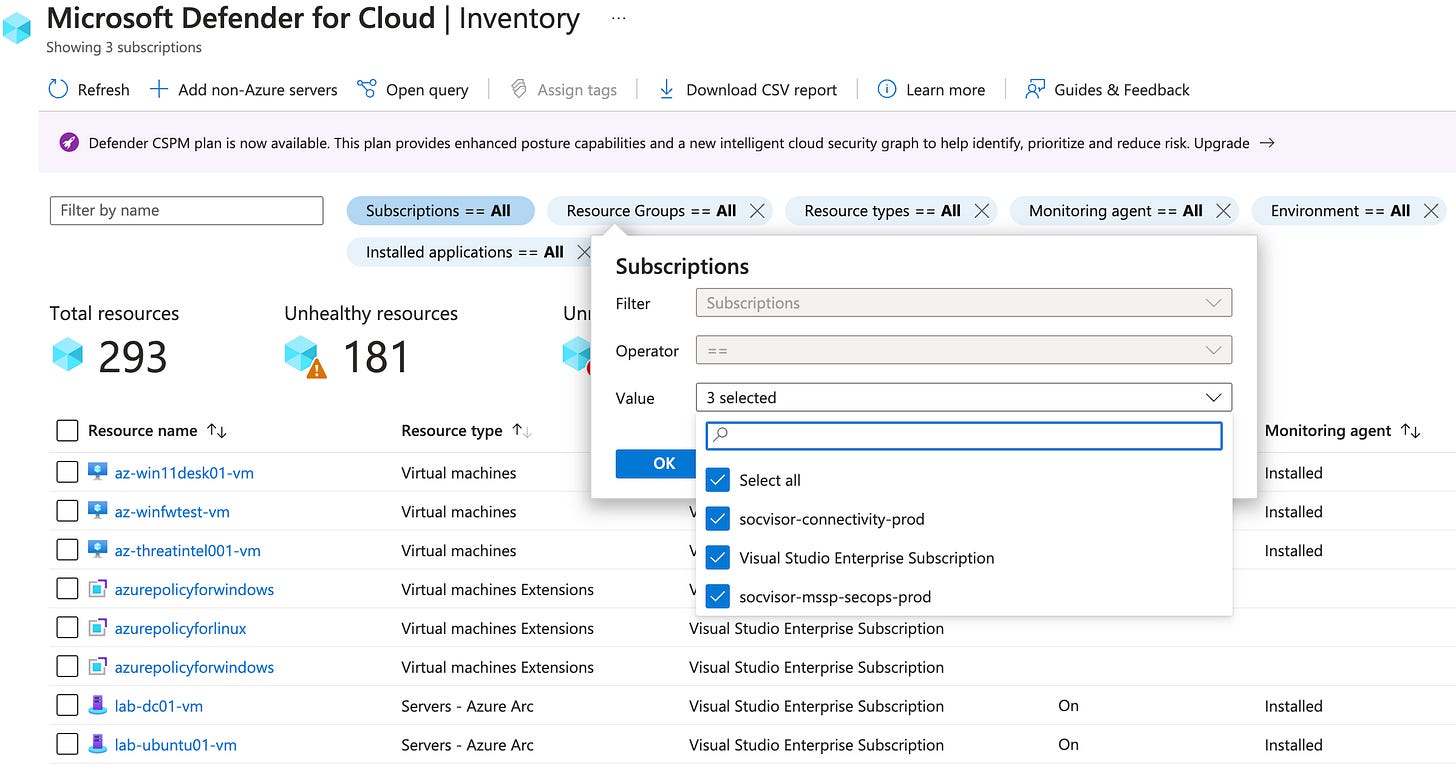
Browsing the Inventory:
Two of the listed subscriptions are cross-tenant via Lighthouse, one is local. Note that here there is no Tenant filter, so the managed subscriptions need to be selected from the Subscription filter.
Alerts in cross-tenant environments:
Looks just like normal alerts in Defender for Cloud. Changing the status, creating suppression rules and other alert actions work as expected.
Management experience
Environment Settings
How do cross-tenant resources look like in the Environment Settings page?
As long as Lighthouse permissions are delegated, you can see the multi-cloud environments in the settings page.
One thing to note is that only for Azure resources it’s shown that the target environment is actually cross-tenant. AWS accounts, GCP projects and DevOps environments found via Lighthouse look as if they would be connected to the local tenant.
So the only way to identify multi-cloud accounts is either documentation, or if you are lucky, a naming scheme where the cloud accounts have the organisation name visible.
For Azure resources note also that Defender for Cloud displays the Tenant ID, not the Azure AD tenant name.
Defender plan settings
Configuring Defender plans for a single subscription in the UI works as you would expect, the experience is identical to local tenant.
The exception here is that for Servers and Containers plans, Agent auto-deployment can not be configured over Lighthouse as those require Owner permissions. The settings are not configurable in the UI:
Of course as multi-tenant situations are usually operating in a larger scale, managing the plan settings via automated scripting or Azure Policy is recommended.
Workflow automation
You can create workflow automations to managed tenants from the Defender for Cloud portal.
If you need to also create the related Logic Apps, remember to include the required roles such as Logic App Contributor in your Lighthouse delegation.
Resources
For more information, be sure to read the official documentation. A few of the important ones are these:
Cross-tenant management in Microsoft Defender for Cloud | Microsoft Learn
User roles and permissions in Microsoft Defender for Cloud | Microsoft Learn
Onboard a customer to Azure Lighthouse - Azure Lighthouse | Microsoft Learn
Deploy Azure Policy to delegated subscriptions at scale - Azure Lighthouse | Microsoft Learn