Maintain a Watchlist on Public IPs in Azure
A simple Logic App for collecting Public IP address resources into a Microsoft Sentinel Watchlist from your Azure tenant
This is a quick rundown on a Logic App I quite often deploy to customers.
The idea is to collect currently existing Azure Public IP addresses into a Sentinel Watchlist, which you can use to identify known assets in your environment and correlate findings and incidents that contain IP address data.
NOTE: This is different from a similarly named watchlist Microsoft provides in the official Sentinel GitHub. That one identifies the known addresses that Microsoft uses to provide global Azure services. The Logic App described here collects IP resources from your own environment, meaning the public attack surface of your own Azure tenant.
Logic App design
The Logic App is nothing very complicated. Mainly we just call Azure API daily, with a query to find the Public IP address resources and write the results to a Watchlist, which gets rotated completely so there is only current data.
You can see the logic here in this Designer screenshot:
At the heart of the Logic App (the HTTP POST action) is just a simple Resource Graph query that finds the IPs and projects a few attributes that we want to collect in our Sentinel Watchlist:
Resources | where type contains 'publicIPAddresses' and isnotempty(properties.ipAddress) | project subscriptionId, name, resourceGroup, properties.ipAddress
That data is put into a CSV table that can be directly inserted into a Watchlist.
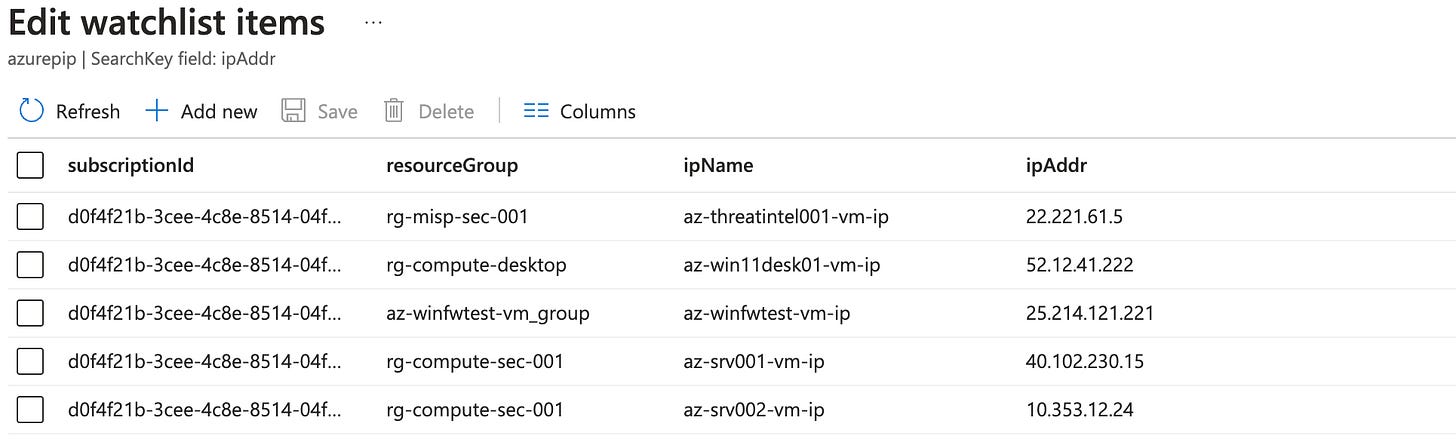
Example results
Here you can see an example of a generated Watchlist in Sentinel:
Deploy the Logic App
You can deploy the Logic App from a template in my Github Repo:
mikoiv/MicrosoftSentinel-Playbooks (github.com)
After clicking the Deploy to Azure button, you need to fill in a few parameters so the Logic App can find your Sentinel instance.
Required permissions
After deployment make sure to grant the following Azure RBAC roles for the Playbook’s Managed Identity:
Azure Reader role for your Tenant Root Management Group for full visibility, or some other scope if you want to limit what data is collected.
Sentinel Contributor role for your Sentinel Resource Group for maintaining the Watchlist.






We are having issues with bad requests within Logic App any ideas?